- Describe the Core Architectural Components of Azure
- Describe Azure Compute and Networking Services
- Describe Azure Storage Services
- Describe Azure Identity, Access and Security
- Reference
Describe the Core Architectural Components of Azure
What is Microsoft Azure?
Azure is a continually expanding set of cloud services that help you meet current and future business challenges. Azure gives you the freedom to build, manage, and deploy applications on a massive global network using your favourite tools and frameworks.
Get started with Azure Accounts

Describe Azure Physical Infrastructure
- Datacenters are grouped into Azure Regions or Azure Availability Zones that are designed to help you achieve resiliency and reliability for your business-critical workloads.
- A Region is a geographical area on the planet that contains at least one, but potential multiple datacenters that are nearby and networked together with a low-latency network.
- Azure intelligently assigns and controls the resources within each region to ensure workloads are appropriately balanced.
- When you deploy a resource in Azure, you’ll often need to choose the region where you want your resource deployed.
- There are also some global Azure services that you don’t require you to select a particular region, such as Microsoft Entra ID, Azure Traffic Manager, and Azure DNS.
- Availability Zones are physically separate datacenters within an Azure Region.
- Each availability zone is made up of one or more datacenters equipped with independent power, cooling, and networking.
- An availability is set up to be an isolation boundary.
- If one zone goes down, the other continues working.
- Availability Zones are connected through high-speed, private fibre-optic networks.
- Region Pairs allows for replication of resources across geography that helps reduce the likelihood of interruptions because of events such as natural disasters, civil unrest, power outages that affect an entire region.
- Most regions are paired in two regions, meaning they are the backup for the region that provides a backup for them, e.g. West US and East US back each other up.
- Sovereign Regions are instances of Azure that are isolated from the main instance of Azure.
Describe Azure Management Infrastructure
Azure Resources
- A resource is the basic building block of Azure. Anything you create, provision, deploy is a resource.
Resource Groups
- Resource Groups are simply groupings of resources. When you create a resource, you’re required to place it into a resource group.
- While a resource group can contain many resources, a single resource can only be in one resource group at a time.
- Resource groups cannot be nested, meaning you cannot put resource group B inside of resource group A.
- When you apply an action to a resource group, that action will apply to all resources within the resource group.
- If you delete a resource group, all the resources will be deleted.
- If you grant or deny access to a resource group, you’ve granted or denied to all the resources within the resource group.
Azure Subscription
- Subscriptions are unit of management, billing, and scale.
- Similar to how resource groups are a way to logically organise your resource groups and facilitate billing.
- There are two types of subscription boundaries that you can use:
- Billing boundary. This type determines how an Azure account is billed for using Azure.
- Access Control boundary. You can use this type to create separate subscriptions to reflect different organisational structures.
- Azure Management Groups provide a level of scope to efficiently manage access, policies, and compliance for many subscriptions.
Describe Azure Compute and Networking Services
Describe Azure Virtual Machines
With Azure Virtual Machines (VMs), you can create and use VMs in the cloud.
Azure can manage the grouping of VMs for you with features like Scale Sets and Availability Sets.
Virtual Machine Scale Sets
- Purpose: Automatically managed and scale a group of identical VMs.
- Features
- Autoscaling. The number of VM instances can automatically increase or decrease in response to demand, or you can set it to scale based on defined schedule.
- Load Balancer.Virtual Machine Scale Sets automatically deploy a load balancer to make sure that your resources are being used efficiently.
- Use Case: Ideal for applications that require high availability and can benefit from automatic scaling, such as web servers, or stateless applications.
Virtual Machine Availability Sets
- Purpose: Ensuring high availability of VMs by distributing them across multiple physical servers.
- Features:
- Fault Domains: VMs are distributed across different physical servers, storage units, and network switches to protect against hardware failures.
- Update Domains: VMs are distributed across different update domains to ensure that not all VMs are rebooted during maintenance.
- Use Case: Ideal for application that require high availability but don’t need automatic scaling, such as database servers or stateful applications.
Describe Azure Virtual Desktop
Azure Virtual Desktop is a desktop and application virtualisation service that runs on the cloud, and enables you to use a cloud-hosted version of Windows from any location.
Describe Azure Containers
Containers are virtualisation environment, are lightweight and designed to be created, scaled out, and stopped dynamically.
Azure Container Instances (ACI)
- Purpose: Run containers without managing the underlying infrastructure.
- Features:
- Fast Deployment.
- Serverless.
- Use Cases: Ideal for simple applications, batch jobs, and microservices that need to start quickly and scale dynamically.
Azure Container Apps
- Purpose: Run microservices and containerised applications without managing complex infrastructure.
- Features:
- Managed Environment.
- Built-in Scaling.
- Integration.
- Use Cases: Ideal for developers who want to focus on building applications without worrying about the underlying infrastructure, especially for microservices and event-driven applications.
Azure Kubernetes Service (AKS)
- Purpose: Full managed Kubernetes container orchestration service.
- Feature:
- Full Kubernetes.
- Scalability.
- Flexibility.
- Use Cases: Ideal for complex applications requiring orchestration, scaling, and management of multiple containers, such as large-scale microservice architectures.
Summary
- ACI: best for simple, fast deployment without managing infrastructure
- Container Apps: best for microservices and event-driven applications with built-in scaling and a managed environment.
- AKS: Best for complex, large-scale applications requiring full kubernetes orchestration and control.
Describe Azure Functions
Azure Functions is an event-driven, serverless compute option that doesn’t require maintaining virtual machine or containers. Similar to AWS Lambda Function.
Describe Application Host Options
If you need to host your application on Azure, you might initially turn to a virtual machine (VM) or containers.
Apart from these, Azure does provide another hosting options, Azure App Service.
Azure App Service enables you to build and host web apps, background jobs, mobile backends, and RESTful APIs in the programming language of your choice without managing infrastructure.
Describe Virtual Networking
Azure Virtual Network and virtual subnets enable Azure resources, such as VMs, web apps, and databases, to communicate with each other, with users on the internet, and with your on-premises client computers.
Azure Virtual Networks provide the following networking capabilities:
- Isolation and Segmentation
- internet communications
- Communicate between Azure resources
- Communicate with on-premises resources
- Route network traffic
- Filter network traffic
- Connect virtual networks
Azure Virtual Networking supports both public and private endpoints to enable communication between external and internal resources with other internal resources.
- Public endpoints have a public IP address and can be accessed from anywhere in the world.
- Private endpoints exist within a virtual network and have a private IP address from within the address space of that virtual network.
| |
| |
| |
| |
Describe Azure Virtual Private Networks
A Virtual Private Network (VPN) uses an encrypted tunnel within another network. VPNs are typically deployed to connect two or more trusted private networks to one another over untrusted network (typically the public internet).
A VPN Gateway is a typical virtual network gateway.
There are two types of VPN supported by Azure VPN:
- Policy-based VPN gateway.
- Route-based VPN gateway.
Describe Azure ExpressRoute
Azure ExpressRoute lets you extend your on-premises networks into the Microsoft cloud over a private connection, with the help of a connectivity provider.
ExpressRoute supports four models that you can use to connect your on-premises network to the Microsoft Cloud
- CloudExchange colocation.
- Point-to-point Ethernet connection.
- Any-to-any connection.
- Directly from ExpressRoute sites.
Describe Azure DNS
Azure DNS is a hosting service for NDS domains that provides name resolution by using Microsoft Azure infrastructure.
Describe Azure Storage Services
Describe Azure Storage Accounts
A storage account provides a unique namespace for your Azure Storage data that’s accessible from anywhere in the work over HTTP or HTTPS. Data in this account is secure, highly available, durable, and massively scalable.
Storage Types
- Blob Storage
- Amazon S3
- Data Lake Storage Gen2
- Amazon S3
- Azure Files
- Amazon EFS
- Queue Storage
- Amazon SQS
- Table Storage.
- Amazon DynamoDB
Describe Azure Storage Redundancy
Azure Storage always stores multiple copies of your data so that it’s protected from planned and unplanned events.
There are multiple options for data storage redundancy
- Redundancy in the primary region
- Locally redundant storage (LRS).
- LRS replicates your data three times within a single data center in the primary region.
- LRS provides 11 nines of durability.
- Zone-redundant storage (ZRS).
- ZRS replicates your Azure Storage data synchronously across three Azure availability zones in the primary region.
- ZRS provides 12 nines of durability.
- Locally redundant storage (LRS).
- Redundancy in the secondary region
- Geo-redundant storage (GRS).
- GRS copies your data synchronously three times within a single physical location in the primary region using LRS.
- It then copies your data asynchronously to a single physical location in the secondary region (the region pair) using LRS.
- GRS provides 16 nines of durability.
- Geo-zone-redundant storage (GZRS).
- GZRS
- Geo-redundant storage (GRS).
Describe Azure Storage services
Azure Storage Platform include following data services:
- Azure Blobs.
- A massively scalable object store for text and binary data.
- Also includes support for big data analytics through Data Lake Storage Gen2.
- Similar to AWS S3.
- Azure Files.
- Managed file shares for cloud or on-premise deployments.
- Similar to AWS EFS.
- Azure Queues.
- A messaging store for reliable messaging between application components.
- Similar to AWS SQS.
- Azure Disks.
- Block-level storage volumes for Azure VMs.
- Similar to AWS EBS.
- Azure Tables.
- NoSQL table option for structured, non-relational data.
- Similar to AWS DynamoDB.
Azure Blob Storage Tiers
- Hot access tier.
- Optimised for storing data that is accessed frequently (for example, images for your site).
- Cool access tier.
- Optimised for data that is infrequently accessed and stored for at least 30 days (for example invoices for your customers).
- Cold access tier.
- Optimised for storing data that is infrequently accesses and stored for at least 90 days.
- Archive access tier.
- Appropriate for data is rarely accessed and stored for at least 180 days, with flexible latency requirements (for example, long-term backups)
The following considerations apply to the different access tiers:
- Hot and cool access tiers can be set at account level. The cold and archive access tiers aren’t available at account level.
- Hot, cool, cold and archive tiers can be set at the blob level, during or after upload.
- Data in the cool and cold access tiers can tolerate slightly lower availability, but still requires high durability, retrieval latency, and throughput characteristics similar to hot data.
- Archive storage stores data offline and offers the lowest storage costs, but also the highest cost to rehydrate and access data.
Identify Azure data migration options
Azure Migrate is a service that helps you migrate from an on-premise environment to the cloud.
Azure Migrate functions as a hub to help you manage the assessment and migration of your on-premises datacenter to Azure. It provides
- Unified migration platform.
- Range of tools.
- Assessment and migration.
Azure Data Box is a physical migration service that helps transfer large amounts of data in a quick, inexpensive, and reliable way. Similar to AWS Snowball.
Identify Azure file movement options
AzCopy is a command-line utility that you can use to copy blobs or files to or from your storage account. You can use AzCopy to upload files, download files, copy files between storage accounts, and even synchronize files. AzCopy only supports one-direction synchronisation. It doesn’t synchronise bi-directionally based on timestamps or other metadata.
Azure Storage Explorer is a standalone app that provides a graphical interface to manage files and blobs in your Azure Storage Account. It uses AzCopy on the backend to perform all of the file and blob management tasks.
Azure File Sync is a tool that let you centralise your file shares in Azure Files and keep the flexibility, performance and compatibility of a Windows File server.
Once you install Azure File Sync on your local Windows server, it will automatically stay bi-directionally synced with your files in Azure.
Describe Azure Identity, Access and Security
Describe Azure directory services
Microsoft Entra ID is a directory service that enables you to sign in and access both Microsoft cloud applications, and cloud applications that you develop. Microsoft Entra ID can also help you maintain your on-premises Active Directory deployment.
- Authentication.
- Single sign-on.
- Application management.
- Device management.
Describe Azure authentication methods
Azure supports multiple authentication methods
- standard passwords.
- single sign-on (SSO).
- multifactor authentication (MFA).
- passwordless.
Describe Azure external identities
An external identity is a person, device, service, etc. that is outside of your organisation. Microsoft Entra ID refers to all the ways you can securely interact with users outside of your organisation.
External identities may sound similar to single sign-on, with External identities, external users can “bring their own identities”.
Describe Azure conditional access
Conditional Access is a tool that Microsoft Entra ID uses to allow (or deny) access to resources based on identity signals. These signals include
- who that user is
- where the user is
- what device the user is requesting access from.
Describe Azure Role-Based Access Control (RBAC)
Role-based access control is applied to a scope, which is a resource or set of resources that this access applies to.
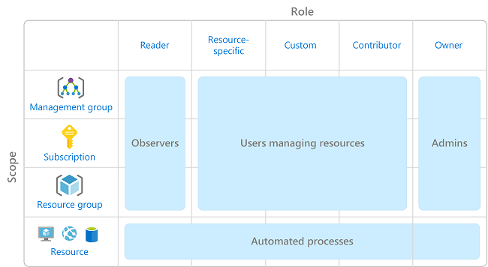
Scope include:
- a management group (a collection of multiple subscriptions)
- a single subscription
- a resource group
- a single resource
Describe zero trust model
Zero Trust is a security model that assumes that assumes the worst case scenario and protects resources with that expectation.
Zero Trust security model is based on these guiding principles:
- Verify explicitly.
- Always authenticate and authorise based on all available data points.
- Use least privilege access.
- Limit user access with Just-In-Time and Just-Enough-Access (JIT/JEA), risk-based adaptive policies, and data protection.
- Assume breach.
- Minimise blast radius and segment access. Verify end-to-end encryption. Use analytics to get visibility, drive threat detection, and improve defenses.
Describe defense-in-depth
The objective of defense-in-depth is to protect information and prevent it from being stolen by those who aren’t authorised to access it.
A defense-it-depth strategy uses a series of mechanisms to slow the advance of an attack that aims at acquiring unauthorised access to data.
- Physical security
- identity & access
- Perimeter
- Network
- Compute
- Application
- Data
Describe Microsoft Defender for Cloud
Defender for Cloud is a monitoring tool for security posture management and threat protection. It monitors your cloud, on-premises, hybrid, and multi-cloud environments to provide guidance and notifications aimed at strengthening your security posture.